Security
Security policies
We know that your business is as important to you as ours is to us, and at the very heart of that is information security. This is why customer trust is at the centre of what we do and why security is a top priority.
01
We are transparent with our security programme to enable you to be feel informed and safe while using our products and services. While our security team continues to expand, everyone at Twinfinity is part of our mission to achieve better security.
We strive to surpass all customers' security requirements, comply with requirements for all relevant standards and certifications and proudly publish details about how we protect customer data.
02
Data security audits and assessments
Being a wholly owned subsidiary to Sweco AB, Twinfinity is subject to the same stringent policies and security measures as defined by our mother company.
Our information security processes and procedures are being audited yearly. In addition, internal audits are being performed each quarter. But that is just compliance. The all-important security work is an ongoing activity.
Twinfinity periodically uses third-party security firms to perform security assessments. These assessments are performed at a minimum of once a year. Any resulting findings are prioritised and addressed according to internal policies and industry best practices.
03
Production environment
We maintain separate and distinct production and development environments for Twinfinity.
To access the production environment, authorised and trained SRE and select engineering team members authenticate using unique strong passwords and hardware based 2FA tools to access the production environment and all such accesses are being logged. We monitor and get alerts of any changes to the production system files or configuration or anomalous security events. For authorised personnel, any workstations must be running current and active anti-virus software and be fully updated. All authorised personnel also undergo special training and extra screening before being allowed access.

04
Development, patch and configuration management
All changes to the Twinfinity production system require review prior to deployment to the production environment.
Automated unit tests are run against production code prior to deployment. Production code is also subject to regularly conducted automated vulnerability scans. All changes are verified in a test environment prior to deployment to production. Patches to web client applications are deployed on a rolling basis, potentially several times per week. All system changes are peer reviewed and patches are deployed based on their importance and criticality.
Production servers are running a LTS (Long Term Support) distribution of their operating system to ensure timely updates are available. CVE lists and notifications are actively monitored and any systems can be patched in a timeline relevant to the severity of the issue.
05
Development process
The Twinfinity development team follows industry standard agile development practices, based on the scrum methodology. We run tests and builds on an ongoing basis, using continuous integration and continuous delivery (CI/CD) tools and practices as much as possible. Industry leading backlog management systems and source control tools are used for all software development, providing a fine-grained, living audit trail of all product decisions, resulting code changes, and releases to the production environment.
06
Employee policies
Security awareness and user data access policies are covered during our employee onboarding as appropriate to the role and employees are updated as relevant policies or practices change. Our employees also sign a confidentiality agreement. All development staff undergo continuous and mandatory security training.
All our employees undergo an extensive interview process before hiring. In addition, our employees with direct access to the production environment undergo an extended background check. Other employees may undergo a check depending on their role. Appropriate NDAs are in place with third parties as appropriate.

07
Your data
remains your data
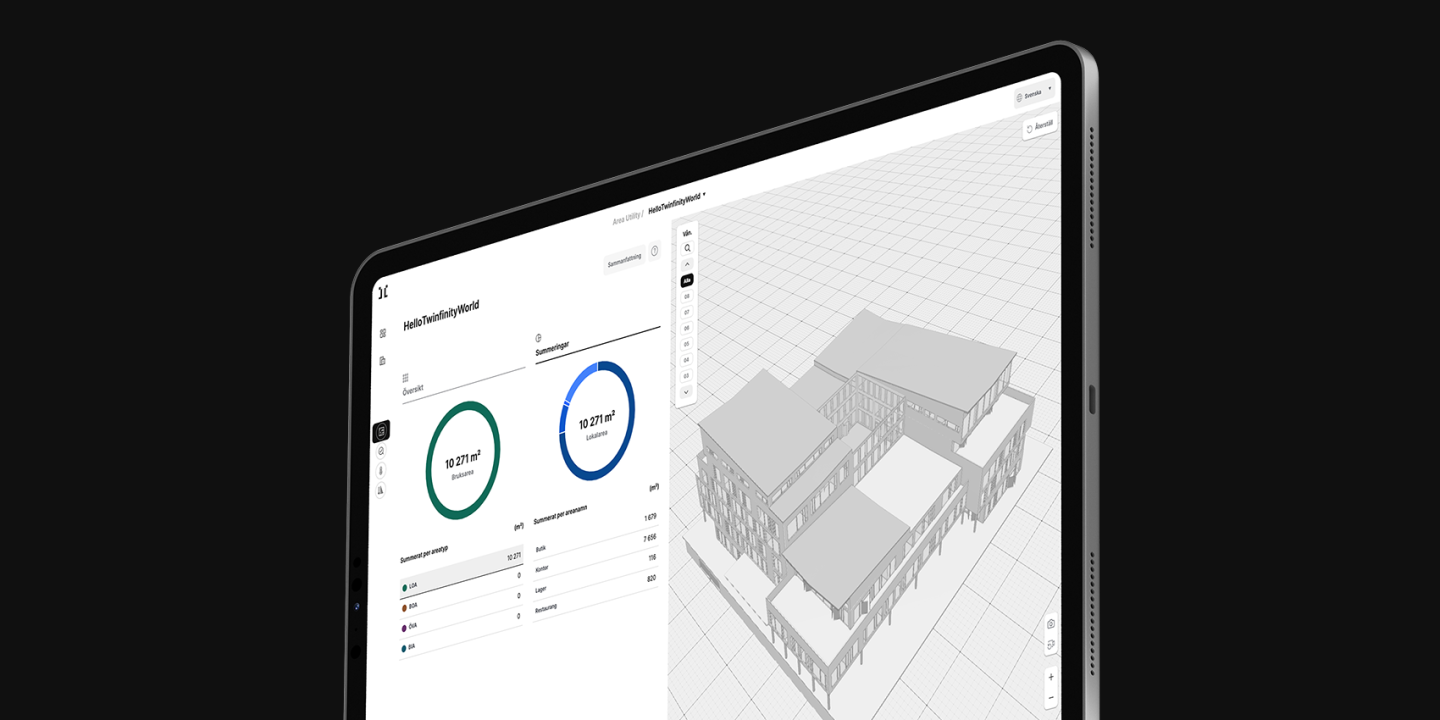
Or platform is divided into two primary components. One, Twinfinity Core, is responsible for breaking down IFC models into data and exposing it via our APIs. The other part, our apps, creates value for our customers through various applications and integrations where the digital building is retrieved from Twinfinity Core and contextualized with operational data from different perspectives (IoT, Sustainability, Business Data, etc.).
This means that our Core platform is responsible for efficiently breaking down models and serving data to clients in an extremely efficient manner with high security. Our customers can choose to build their own applications where models are combined with other data sources to create value for different actors in different contexts. The applications is run in our clients browsers, meaning that Twinfinity AB, will never know anything about the integrated data in an application buildt by a customer.
Further questions?
We work hard to protect your data and to give you the information you need to make an informed decision about Twinfinity security.